Threat Watch
Instantly assess your cybersecurity health with actionable insights across critical risk categories.
Visit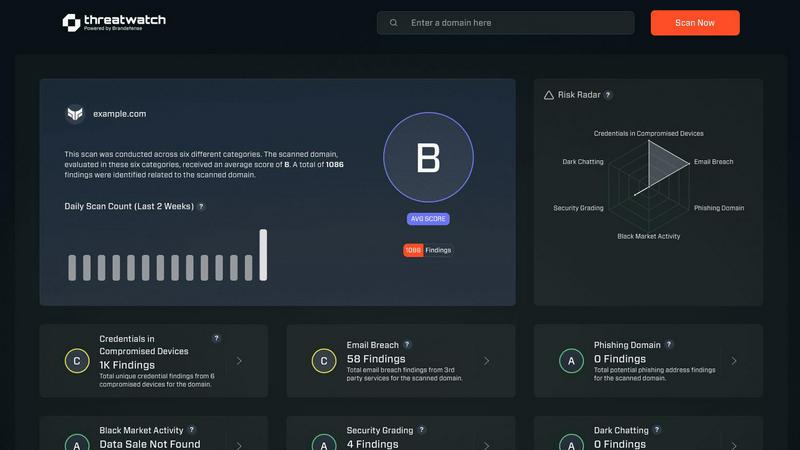
About Threat Watch
Threat Watch is a unified cybersecurity intelligence platform designed to provide organizations with a comprehensive and real-time view of their digital security posture. It functions as a centralized diagnostic tool for cyber health, continuously analyzing an organization's assets, vulnerabilities, and exposures across the clear, deep, and dark web. The product is engineered for IT security teams, risk management professionals, and business leaders who need to move from reactive security measures to a proactive, intelligence-driven strategy. Its core value proposition lies in its ability to consolidate disparate threat data into a single, actionable dashboard. By automating assessments and delivering prioritized insights, Threat Watch empowers organizations to identify critical risks—such as compromised credentials, breached accounts, and vulnerable devices—and mitigate them faster, thereby reducing the window of opportunity for attackers and strengthening overall resilience.
Features of Threat Watch
Comprehensive Cyber Health Scan
This foundational feature provides a rapid, automated assessment of your organization's security posture across multiple critical categories. It evaluates assets, identifies vulnerabilities, and scans for exposures like compromised credentials and phishing addresses, delivering a clear, instant snapshot of your cyber health to serve as a baseline for ongoing protection and improvement efforts.
Real-Time Dark Web & Breach Monitoring
Threat Watch continuously patrols the dark web, hacker forums, and breach databases in real-time. It actively searches for your organization's stolen data, including employee credentials, intellectual property, and confidential information, providing immediate alerts when your assets are found in illicit spaces, enabling swift response to potential threats.
Compromised Device & Account Identification
The platform meticulously identifies devices within your network that may be compromised or acting maliciously, alongside employee accounts that have been breached in third-party incidents. This precise identification is crucial for containing threats, initiating password resets, and isolating affected systems to prevent lateral movement by attackers.
Phishing & Impersonation Detection
Threat Watch scans for phishing campaigns and fraudulent domains that impersonate your brand or target your employees. By detecting fake websites and malicious email addresses designed to deceive your staff or customers, this feature helps protect your organization's reputation and prevents successful social engineering attacks.
Use Cases of Threat Watch
Proactive Risk Management for IT Security Teams
Security operations centers (SOCs) and IT teams use Threat Watch to shift from a reactive, alert-driven model to a proactive risk management stance. The platform's unified intelligence allows them to prioritize patching, configuration changes, and incident response based on actual exposure data, optimizing resource allocation and closing security gaps before they are exploited.
Executive & Board-Level Security Reporting
CISOs and risk officers leverage the clear, dashboard-driven "cyber health" picture provided by Threat Watch to communicate security status effectively to non-technical executives and board members. It translates complex threat data into understandable metrics, facilitating informed decision-making and securing budget for necessary security initiatives.
Third-Party & Supply Chain Risk Assessment
Organizations can extend their security monitoring to assess the risk posed by vendors and partners. By scanning for breaches and exposures related to third-party domains and credentials, Threat Watch helps identify weak links in the supply chain, enabling companies to manage third-party risk more effectively and enforce stricter security requirements.
Post-Breach Investigation and Damage Control
Following a security incident, Threat Watch serves as a critical tool for forensic investigation and damage assessment. It helps security teams understand the full scope of a breach by identifying all compromised accounts, devices, and data points, ensuring a thorough remediation process and helping to prevent recurrence.
Frequently Asked Questions
How does Threat Watch discover my company's data on the dark web?
Threat Watch employs a combination of automated crawlers, specialized sensors, and integrations with global threat intelligence feeds to monitor dark web marketplaces, private hacker forums, and paste sites. It uses targeted queries based on your organization's digital footprint (like domain names, key employee names, and brand terms) to find relevant stolen data, such as credential dumps and leaked documents.
What is included in the "Cyber Health" score or assessment?
The Cyber Health assessment is a multi-faceted evaluation of your organization's security posture. It typically analyzes categories including exposed credentials, breached employee accounts, compromised devices within your network, phishing domains targeting your brand, and the presence of your sensitive data on the dark web. The resulting score provides a prioritized overview of your most critical risks.
Do I need to install any software on my network to use Threat Watch?
Threat Watch is primarily a cloud-based, external monitoring solution. For features like compromised device identification, some lightweight integration or agent-based deployment may be suggested for full visibility. However, the core dark web, breach, and phishing monitoring capabilities require no internal software installation, allowing for a quick and non-intrusive deployment.
How quickly will I be alerted if my data is found?
Threat Watch is built for real-time intelligence. Alerts are generated and pushed to your dashboard and configured notification channels (like email or SIEM integration) as soon as a relevant match is discovered during its continuous scanning process. This ensures your team can react to threats within minutes or hours, not days or weeks.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
aVenture
aVenture is an AI platform for institutional-grade research on private companies and venture capital markets.
iGPT
iGPT turns messy email data into trusted, context-aware answers for enterprise agents.